Table of contents
Hashicorp vault in practical way
HashiCorp Vault is a secure mechanism for managing and delivering secrets. Even though it may seem basic when it comes to knowing how to store and recover credentials, this post strives to tackle advanced concepts of how and why HashiCorp Vault can be useful in the organization.
1. API Keys Reimagination Service Accounts Construction And More: Advanced Use Cases
It doesn’t end with storing secrets. It goes further and that is the ability to create and deliver dynamic secrets while at the same time looking at head-on a few advanced features: Targeting reconstruction of services assets by designating different ranges of upper limits of the various accounts being created for each application while being given appropriate permissions. Dynamically provision API keys with limited scopes and expiration times, enhancing security and compliance. Create and control databases Build unique credentials and limit their time span for every connection built to the database so as to lower the risk of exposure in case of a breach.
2. AWS Secrets Engine Exploring Secret Engines And Delving Into The Basics
Vault delivers a comprehensive collection of secret engines which includes: AWS Secrets Engine Enables a perfect synchronization with AWS enabling a user to securely integrate AWS credentials along with IAM and several other sensitive, sensitive information saving resources.
GCP Secrets Engine: Authenticate Google Cloud Platform credentials, service accounts and other Vault managed secrets.
Azure Key Vault Engine: Interact with Azure Key Vault as a means of utilizing its features for the storage of the keys and secrets.
3. Secret versioning, recovery and rotation
Versioning: Vault helps users to keep all the secrets changed and creates the ability to look into past activities and changes done inside VPol Vault and even allows to revert to such versions when necessary.
Recovery: Establish appropriate recovery plans to decrease the consequences of unintentional losses or breaches. This in turn might include the use of Vault’s audit logs, backups, and disaster recovery strategies.
Automated Rotation: Apply time based automated policies in changing of secrets that could include database passwords, API keys, and SSH keys on a regular rotating basis, In this case, the exposure is reduced significantly and your overall security posture enhances.
4. Enhanced authentication capabilities
More Than Tokens: Take advantage of more extensive authentication capabilities like AWS IAM, Azure AD , LDAP , among others to support existing identity and access management technologies.
Tokenization: Take advantage of tokenization to augment security and scalability by limiting the range of tokens used for such purposes. Tokens can be used as controlled and multifaceted authentication credentials allowing thieves and abusers of such credentials to restrict the access to such tokens.
5. Using the Vault CLI and API in the Appropriate Way
Dynamic Secrets: You can use the Vault CLI and API to create and deploy new secrets for new applications and services.
Secret Engines: The use of API enables sends to the different secret engines and manages the secrets including the settings.
Authentication: The Integration of an external identity provider is a form of authentication and can be done using the Vault CLI and API.
Case studies that represent real-world scenarios
Protecting Kubernetes Secrets:
Based pods, Kubernetes environments can use the AWS Secrets Engine to offer and manage secrets.
To reduce the chances of exposure, secrets can be updated on a regular basis.
Only the pods that are authorized can access certain secrets, which can be implemented using rbac.
Maintaining Security on Studdathed Feralobrstrength Database Connections:
Applications connecting to a database are provided with temporary credentials that are unique and limited to that application only.
Having automatic improvement in passwords will increase safety and lower chances of letting unauthorized users gain access.
Intervening with database activities after certain credentials have been revealed in order.
Maintaining Safety with API keys:
Assigning named scopes on the API keys assets in when they are probated or expired is highly effective.
Making the access and usage of the API key more complex than normal should limit the targeted application users and developers.
Lastly, avoiding suspicious activities by monitoring the actions carried out by the API key Should be well placed.
Visuals
Vaults Architecture:
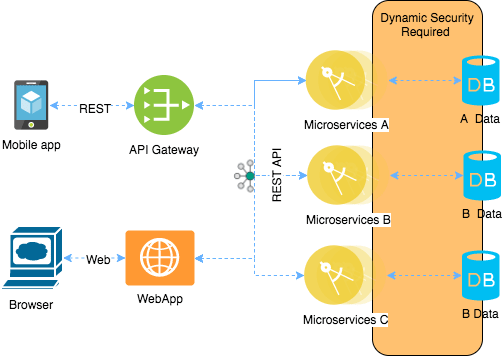
We illustrate how secrets flow from a Vault to a microservices application by showing the main parts and their interactions.
Secret Rotation Flow:
This video shows a sequence of events that make up the automated process of secret rotation, as well as the triggers and alerts.
Code Example (Python)
import hvac
client = hvac.Client()
# Reading a secret from Vault
secret = client.secrets.kv.v2.read_secret(path='secret/my-secret')
print(secret['data']['my-password'])
# Creating a dynamic secret
dynamic_secret = client.secrets.kv.v2.read_secret(path='secret/my-dynamic-secret')
print(dynamic_secret['data']['value'])
Having demonstrated some of the features of HashiCorp Vault, this post presents various resources:
Official Vault documentation: https://developer.hashicorp.com/vault/docs
Vault Tutorials: https://developer.hashicorp.com/vault/tutorials
Vault Community: https://www.vaultproject.io/community
These advanced concepts, when effectively adopted, will assist your organization in achieving enhanced security, operational efficiency, and the control you desire over your secrets management.
Happy Learning!
#hashicorp #vault #hashicorpcommunity #hug #hugpune #devops
