With the ever-evolving cyber threats and the increasing need for improved security, it's no wonder that many businesses are looking to Amazon Web Services (AWS) as their provider of choice. From data protection to identity and access management, AWS offers a wide range of security features and services designed to help protect your applications and data. But while AWS is incredibly secure, it’s up to you as the user to ensure proper implementation of security measures. There are a number of steps you can take to ensure your applications and data remain safe, including understanding the basics of Amazon security fundamentals. In this blog post, we’ll break down how you can use AWS security features and services to safeguard your business. We’ll cover everything from basic best practices, such as using strong passwords and implementing multi-factor authentication (MFA), to more advanced topics like configuring IAM roles for application users. By following these guidelines, you’ll understand how to secure your applications on AWS and keep your data safe from malicious actors or cyber threats.
Why is it important to secure your applications and data in the cloud?
This is a comprehensive guide to protecting your applications and data in the cloud. With this step-by-step guide, you’ll learn how cloud security solutions provide a holistic view of your security posture and enable you to respond quickly to threats. Cloud security solutions can also help you detect, respond and recover from incidents faster and more efficiently, while helping reduce costs associated with data breaches and other security incidents. Plus, they help protect against data loss, unauthorized access and data corruption. AWS Security Fundamentals equips you with the tools necessary to secure your applications and data in the cloud so that you can focus on building great products for your customers.
The components of AWS security
AWS Security Fundamentals is a step-by-step guide to safeguarding your applications and data. It’s based on the shared responsibility model between Customers and AWS, wherein customers are responsible for configuring the security settings of their AWS resources, while AWS provides a range of security services and features to secure the infrastructure, data, and applications.
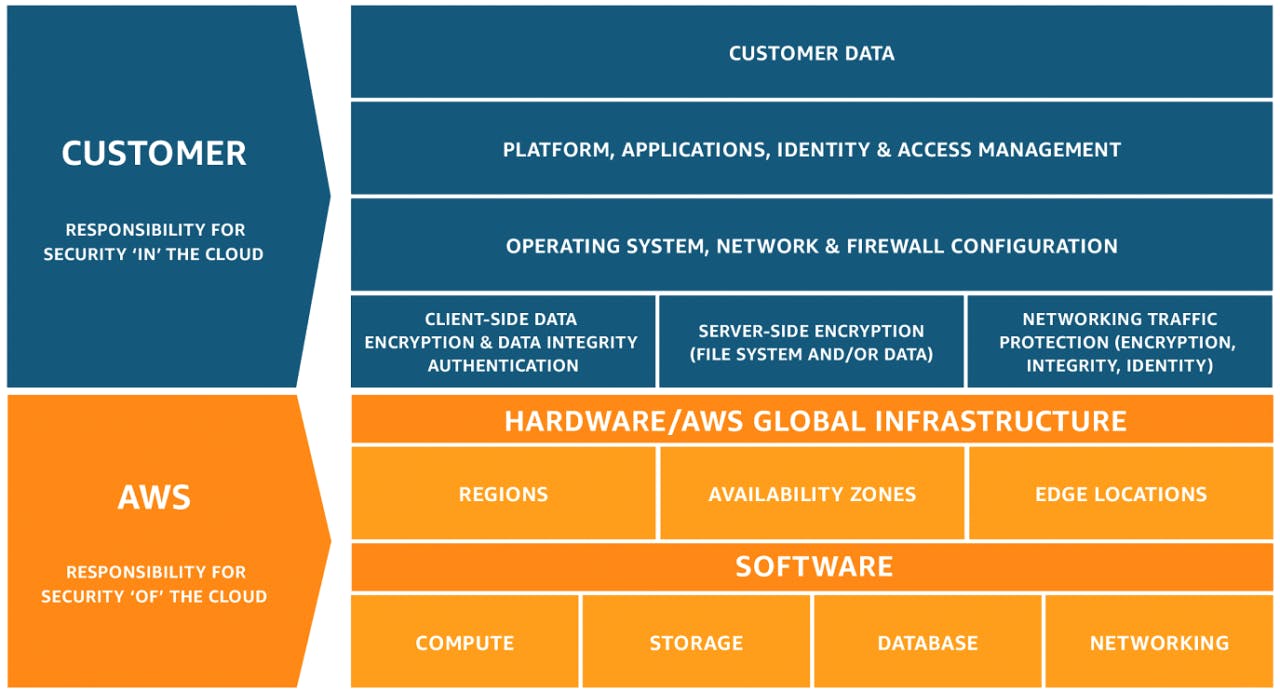
The core components of AWS Security include identity and access management, network security, encryption, monitoring and logging, as well as a variety of tools to help customers securely store, manage, and protect their data and applications. With this guide in hand you can be confident that your business is safely secured against unauthorized access with state-of-the art security solutions from Amazon Web Services.
How to protect your data in the cloud environment.
As a business owner or IT professional, it’s important to secure your applications and data hosted in the cloud. AWS offers you an easy-to-follow roadmap that will help keep your applications safe and secure. This guide is designed to ensure your cloud-based data is encrypted both in transit and at rest, as well as monitor your cloud infrastructure for any suspicious activity or threats. Additionally, this guide will show you how to utilize multi-factor authentication for user access and login credentials, implement industry standard security protocols to protect your data from unauthorized access, and regularly backup your data and store it offline to prevent accidental or malicious data loss. Stay one step ahead of the hackers with AWS Security Fundamentals: A Step-by-Step Guide to Safeguarding Your Applications and Data.
Best practices for designing secure applications on AWS.
Setting up the right mechanisms to protect your applications and data on AWS is critical. Thankfully, you have a range of security tools at your disposal that will help you achieve this goal. With the step-by-step guide of AWS Security Fundamentals, you can learn how to best utilize AWS Identity and Access Management (IAM) to control access to AWS resources. You can also use Amazon CloudWatch to monitor and log activities, as well as Amazon Virtual Private Cloud (VPC) for securing the network environment. Additionally, you'll be able to encrypt data at rest with AWS Key Management Service (KMS), and track user activity and API usage with AWS CloudTrail. All these steps will help establish a secure foundation so that you can develop applications without worrying about potential threats or breaches.
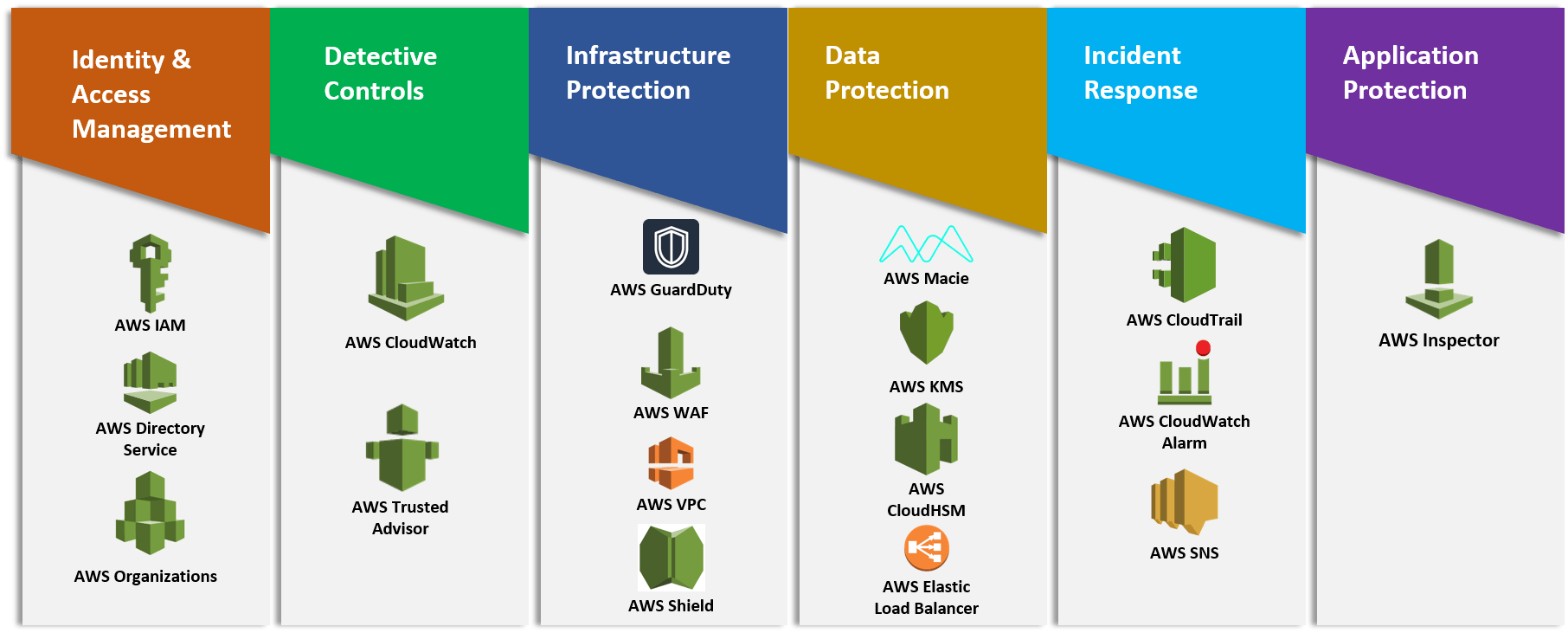 We will dive deep into these best practices in upcoming posts, stay tuned!
We will dive deep into these best practices in upcoming posts, stay tuned!
Securing applications and data in the cloud is an essential part of using cloud services, such as AWS. AWS provides a wide range of security components to help protect your applications and data. To ensure that your applications and data are properly secured, it is important to understand the different components of AWS security and how to use them effectively. Additionally, there are best practices for designing secure applications on AWS that should be followed in order to keep your environment safe. By following these guidelines and taking advantage of all the security features provided by AWS, you can ensure that your applications and data are properly secured in the cloud environment.

